Table of Contents
Hacking RF controlled power switches with HackRF
In order to learn more about GNU Radio and HackRF, so that tackling more complex scenarios like darc-side-of-munich-hunting-fm-broadcasts-for-bus-and-tram-display-information-on-90-mhz become easier, it was time to go for a much simpler training target:
Those cheap RF controlled wall plugs you can use to remote control the power outlets. Now, I'm not talking about FS20, x10 or HomeMatic devices but the really cheap ones you can usually buy in sets of three combined with a handheld remote controller for 10-20 EUR.
The goal here is to find out, how long it actually takes to reverse engineer this particular (at least 10 year old) system and achieve full remote control capability using HackRF and other open-source tools.
Episode I
This episode concentrates on the receiving side (identification, verification and analysis) while Episode II will be focused on using the HackRF as a transmitter, to finally own the system.
Identification
It's necessary to know WHERE to look in order to try to figure out WHAT is going on. As ever so often, these devices don't indicate what frequency/band they are using, which basically makes it a needle in a haystack. A frequency counter might help here but none is available so let's see how much can be achieved by simple deduction, guessing and luck.
Strategies to reduce the Haystack
Per definition the RF band stretches from 3 kHz to 300 GHz, so, theoretically, our signal candidate could be anywhere in there. But in practice, even the HackRF can only observe a 20 MHz wide strip of the complete spectrum at one time, so we would have to “scan” through the whole spectrum in 20 MHz steps to cover what we can with a HackRF, between 10 MHz and 6 GHz. What now? Like so often: Sun Tzu already said:
Hence the saying: If you know the enemy and know yourself, your victory will not stand in doubt; if you know Heaven and know Earth, you may make your victory complete.Sun Tzu - The Art of War - 10. Terrain (31)
He obviously hints to us that knowing our physical terrain/ground “know Earth” is at least as important as knowing the invisible RF terrain “know Heaven”. If you're an old-school HAM this may be obvious to you but if you're coming from a completely different background you will be able to work much faster, when you know your terrain, the different bands and what usually goes on there. Search the web for band plans and frequencies, tune in, have a look around, simply get familiar with it. So, for those unfamiliar, let's take a look at some of the shortcuts used here to drastically improve hit probability:
Maxwell's rotating-in-his-grave razor
Guessing by the size and weight of the transmitter, there is no long antenna wire in there (Long antenna = long wavelength = low frequency), which leads to the conclusion that we could start to ignore everything below 27MHz. 27MHz was commonly used for RC models but most of them have moved to 2.4 GHz and some esoteric switches also use this frequency. Let's put it aside as a secondary band to probe.
Chrono's universally applicable make-it-cheapa razor
When every company has the necessity to grow, and operate more profitable, then, if the costs to produce just the cheapest, barely usable or insecure product plus the costs of having a kick-ass marketing team to brainwash people into buying crappy products is less than the costs of simply making a solid and reliable product (which almost always is the case eventually) - every board in the world is basically forced to do so or they would simply not act in the interest of the company, which is profit and growth. Let's apply it here:
As a designer/manufacturer, you would need to have a frequency usage permit/license for each individual frequency per each country where you would like to offer the product. Since this is a lot of administrative overhead (people cost the most), not to mention the added individual license costs. As a result, many products use the industrial, scientific and medical (ISM) radio bands to make them cheaper (broad availability of ready-to-use components & knowledge) and easy to export/import.
These bands therefore have a much higher probability of carrying our signal candidate than the rest of the available RF spectrum, so let's target the usual ISM suspects first. In Europe 433 and 868 MHz are commonly used for remote controls (even cranes), data/sensor telemetry (weather stations and the like) and much more.
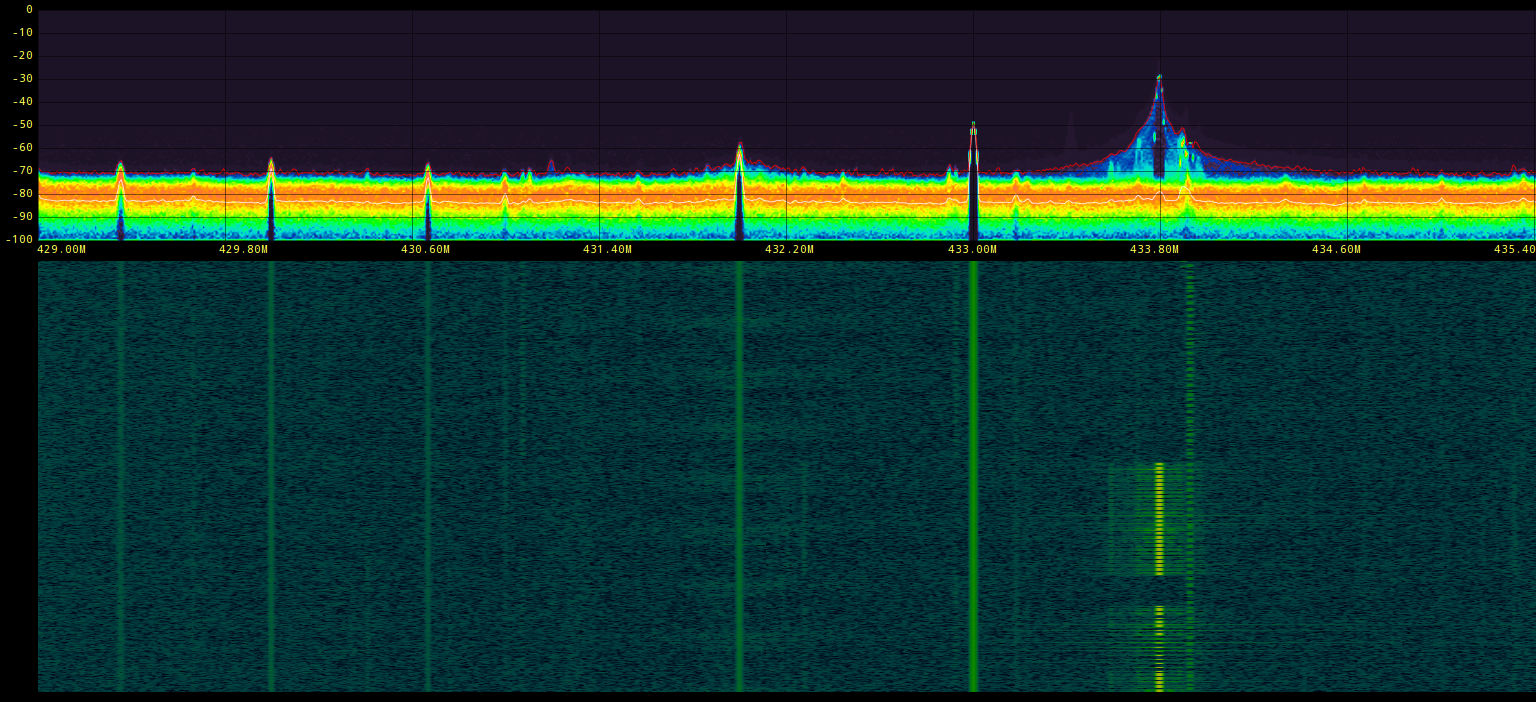
Let's pick 433 MHz first, fire up osmocom_fft, gqrx, SDRangelove or any other SDR receiver with a spectrum analyzer/waterfall display tuned to 433 MHz.
$ osmocom_fft -f 433000000 -s 8000000 -W -S -F --fft-size=1024
Now we just have to observe the spectrum/waterfall while pressing buttons on the remote.
And baaaaaaam, right there it is, centered on 433.795 MHz, lucky shot :)
Analysis
We now know where we have to look so it's time to build a simple receiver to see what happens when we press buttons on the remote control to find out how the receiver distinguishes which specific buttons we have pressed.
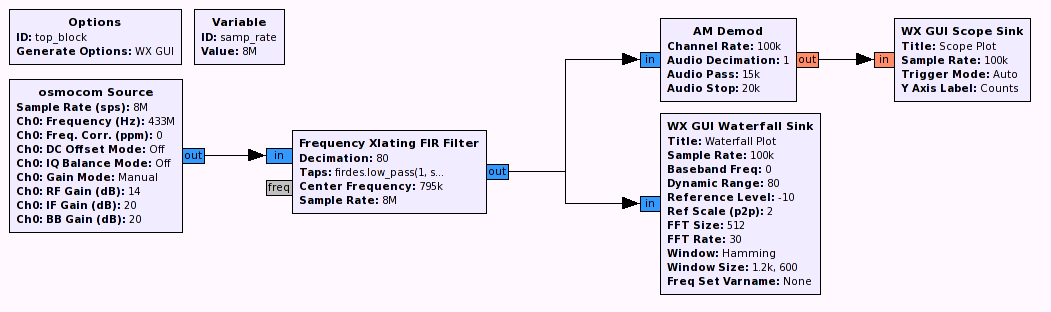
A simple receiver
Again we can deduce that economic reasons will exclude complicated modulations or security so we start by building the most simple receiver to look at the signal.
FIR Filter Tap:
firdes.low_pass(1, samp_rate, 5e3, 2.5e3)
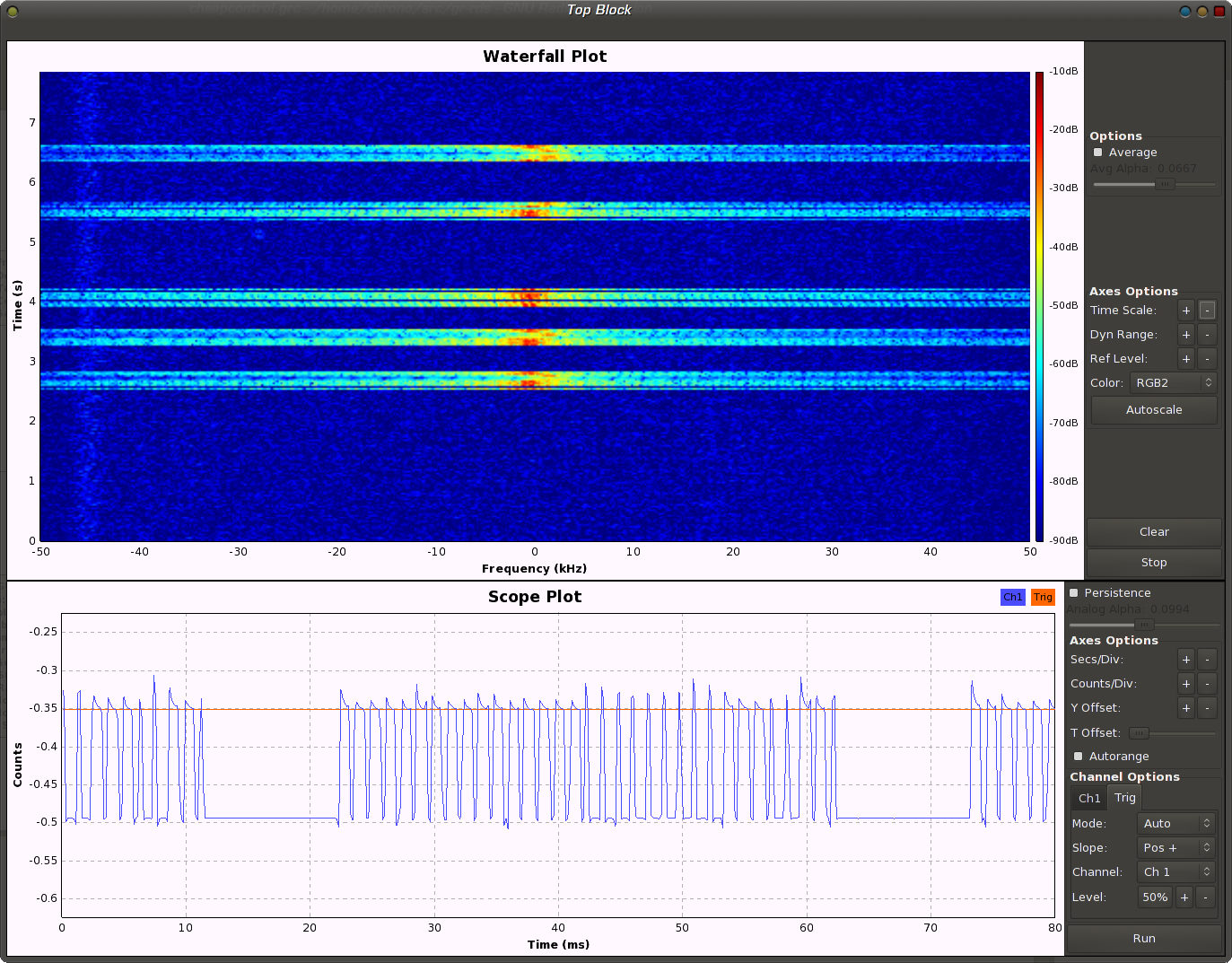
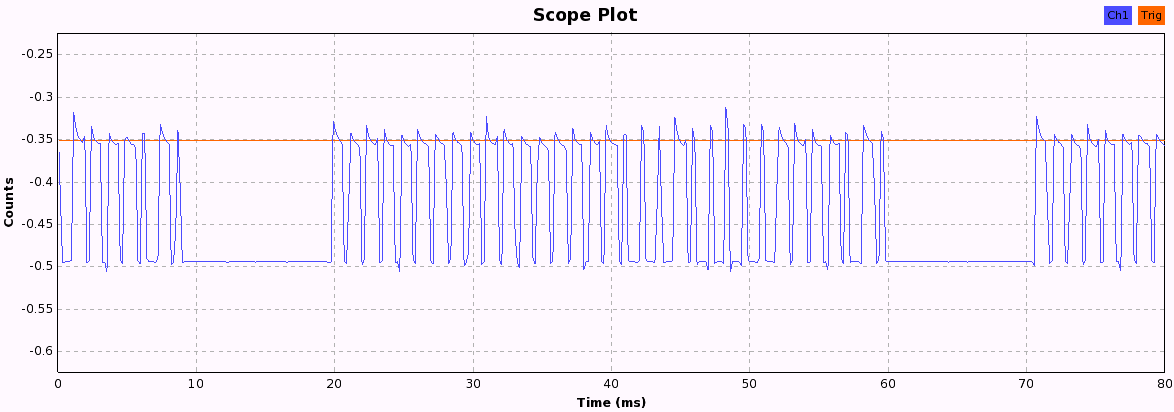
Signal Pattern
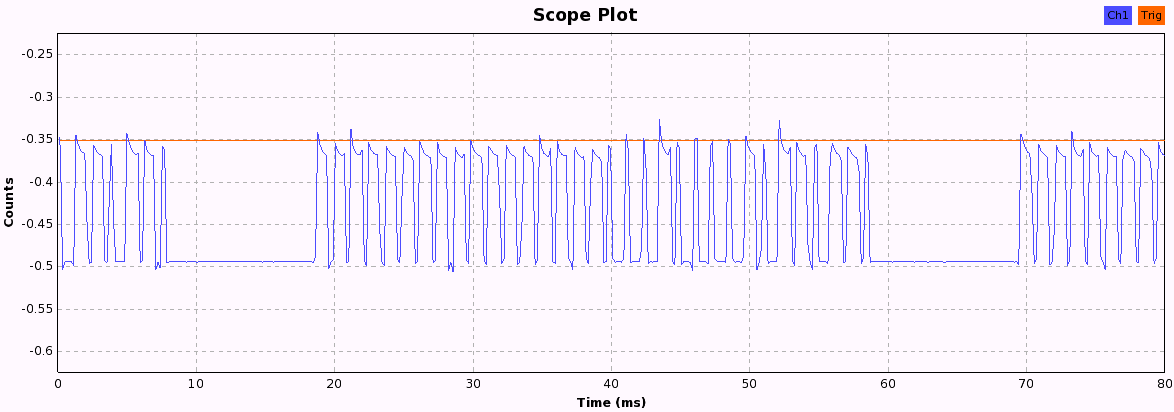
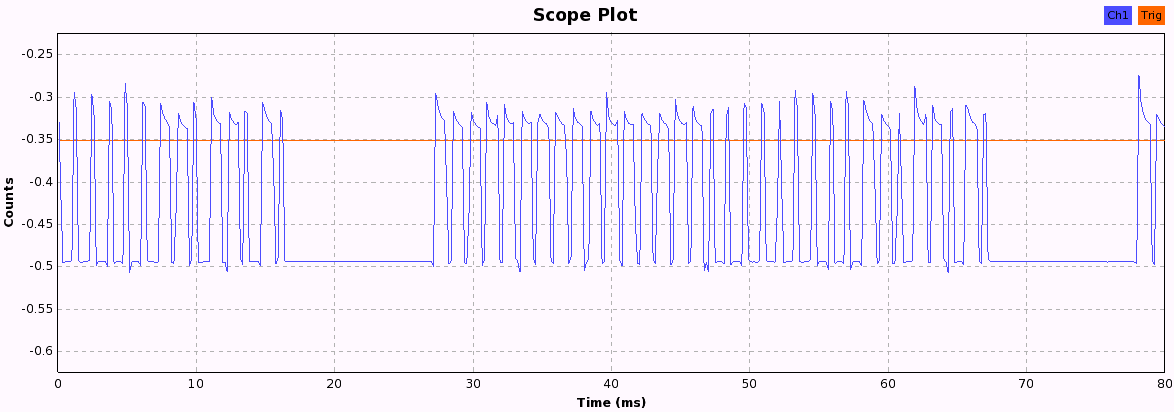
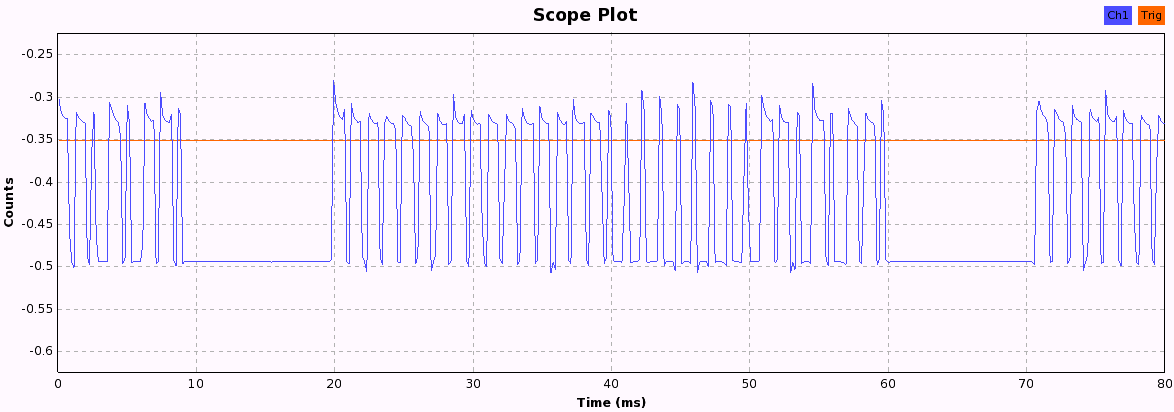
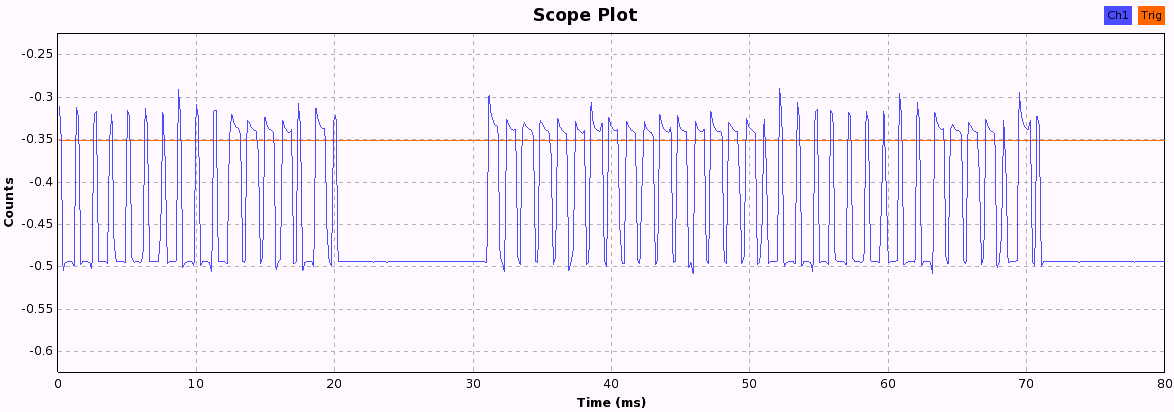
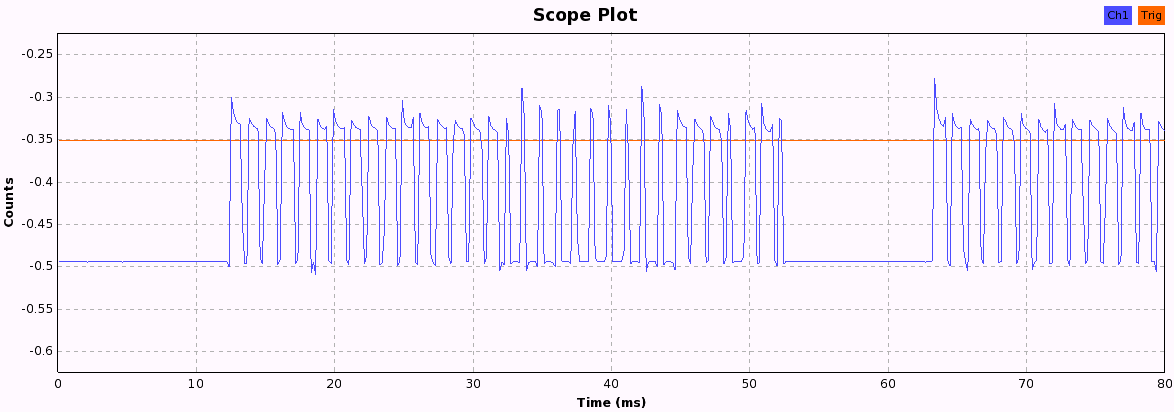
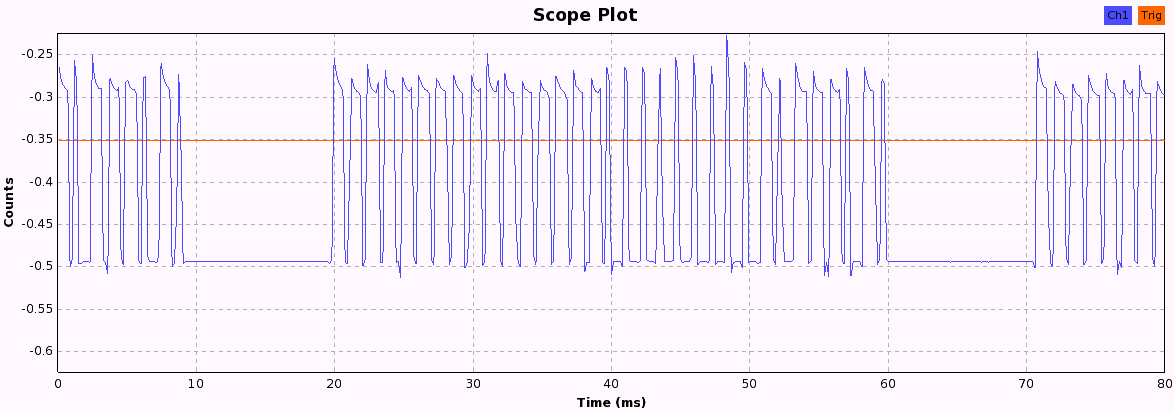
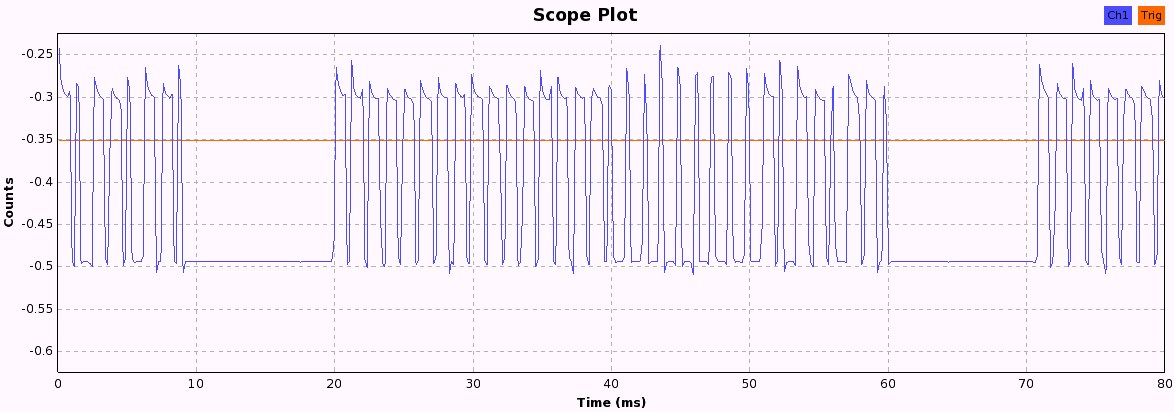
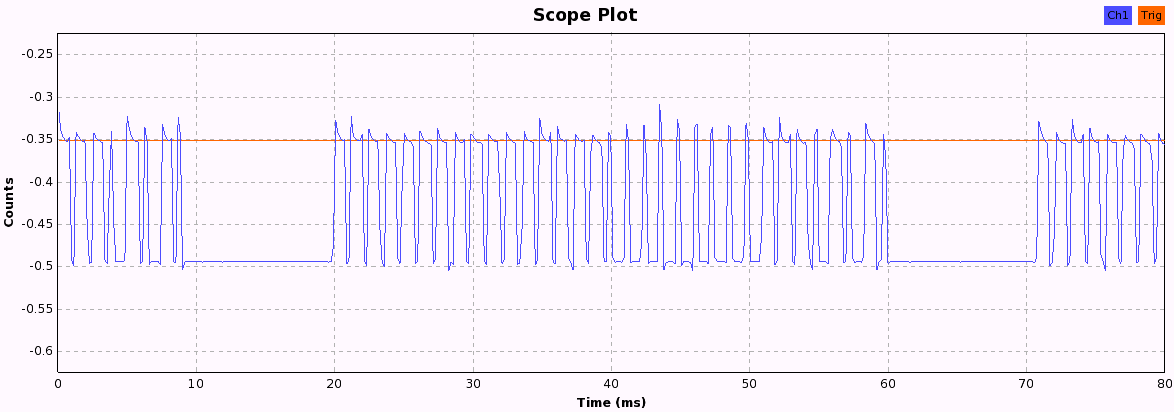
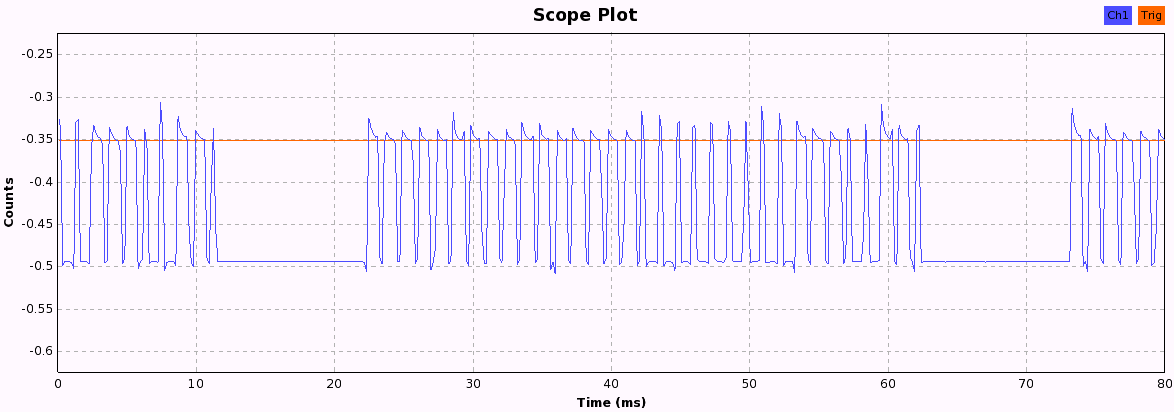
Now we just have to press the buttons and look at the pattern each button produces. When pressing a button, the following bit patterns are sent over the ether, each repeated three times with a 10ms pause in between, probably to increase the chance that the weak signal isn't lost due to other ISM transmission interference. After a while, the pattern becomes quite obvious and we can start to assign 1 and 0 values to the long and short periods we see in these 33-bit patterns.
The whole process took a little less than an hour, just using GNU Radio and a HackRF (could have been done with an RTL-SDR device as well. The next steps will be covered in Episode II, where we can try to reproduce this pattern with a transmitter we'll build with GNU Radio. This will also serve as a chance to try something I'd like to call:
Full Band IQ Replay Attack.
Instead of trying to find specific frequencies and modulations in order to build a narrow target transmitter, it should be equally feasible to just “record” a wide target band by capturing 10MSps raw IQ data and try to send this raw IQ data as it was received (replay). This would be a very crude approach requiring almost no knowledge about the specific implementation but could be disastrously fast and effective when applied successfully, in many situations.